Prayervigils.net is a free prayer vigil site where communities around the world can create a prayer vigil for their events in their own time zones.
To access Prayervigils.net, open your preferred web browser and navigate to www.prayervigils.net. The site is accessible on desktop computers, tablets, and smartphones.
You simply click the vigil sign up button on the home page, wait a few minutes for your vigil to be approved. (please note it’s only the system admins that can make amendments to typing errors etc.)

Once the vigil is approved you will receive an email link to your vigil. All that is left for you to do is to share the link and people can sign up on your own link and commit your event in prayer by praying during their requested time slot.
The home page displays featured vigils.
Use the search bar to find vigils based on keywords or event descriptions
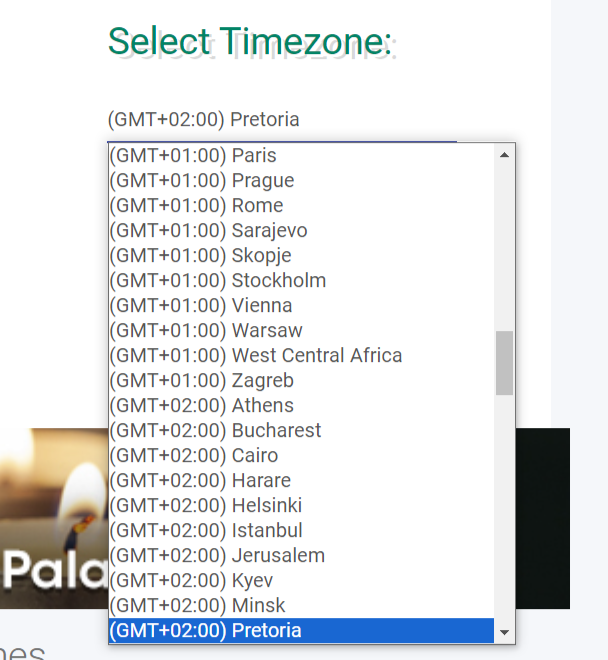
Click on a vigil to view its details. Change the time zone and sign up on the desired prayer slot time. (please note its only the system admins that can make amendments to typing errors etc)
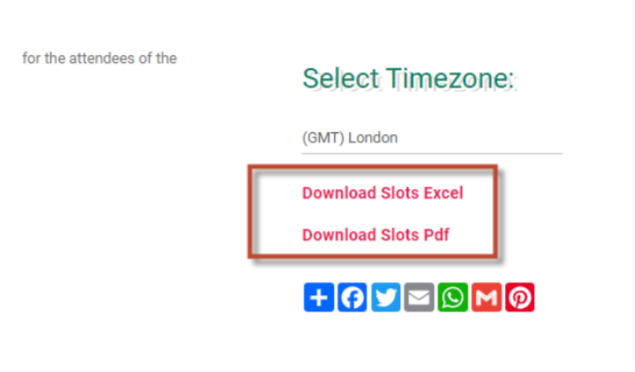
Select the Time Zone relevant to user location and signup to fill out the form.
The notification email gets sent to the user who signs up for a prayer slot, and the reminder email gets sent out to signed-up users 2 days before the event.
To export the list of users who have signup to participate in prayer for the event you open, you open the event and on the top right you select the format you want to export with.
If you experience technical difficulties, ensure you have a stable internet connection and try accessing the site through a different web browser. If the problem persists, email technical support at [email protected] or use the contact form found on the contact us page www.prayervigils.net/contactUs. When sending a query please add the name and link of the event that needs changes, state the problems clearly and if possible also add screenshots.
We have Cloudlfare firewall in place.
Cloudflare WAF, or Web Application Firewall, is a security service that stands like a guard between your website or web application and the internet. It acts as a shield, analyzing and filtering incoming traffic to block malicious requests and protect your application from a wide range of cyberattacks. Here's a breakdown of what Cloudflare WAF does:
HTTP traffic: It examines every incoming HTTP request coming to your website or application. Suspicious patterns: It scans for patterns and characteristics that indicate malicious intent, such as SQL injection attempts, cross-site scripting, bots, and other attack methods.
Rulesets: Cloudflare WAF relies on sets of rules called "rulesets" to identify and block malicious traffic. These rulesets cover a wide range of known vulnerabilities and attacks. Machine learning: It utilizes machine learning to detect even newer and more sophisticated attacks that haven't been predefined in the rulesets. Custom rules: You can also create your own custom rules to fine-tune the protection for your specific needs.
Improved security: It significantly reduces the risk of successful cyberattacks on your website or application. Global network: Cloudflare's global network processes over 2 trillion requests daily, keeping you updated with the latest security threats and providing real-time protection. Easy to manage: The WAF is cloud-based and requires minimal configuration, making it suitable for users of all technical expertise. Scalability: It can handle fluctuating traffic volumes without compromising performance or security.
Cloudflare WAF offers various plans with different levels of protection and features. While it's a powerful security tool, it's not a silver bullet. It's essential to employ other security practices alongside Cloudflare WAF for complete protection.
In addition to this the website is updated monthly to the latest version of wordpress.
Acess to the admin section is controlled to approved users only with different roles and permissions including editor / customer and admin.
Websites must obtain informed consent from users before collecting their personal information. This means clearly explaining what information is being collected, how it will be used, and who it will be shared with. Consent must be freely given, specific, informed, and unambiguous. This means users must not be pressured to give consent, and they must understand what they are consenting to.
Personal information can only be collected and used for a lawful purpose that is related to the website's functions or activities. This purpose must be clearly stated in the privacy policy.
Websites should only collect the minimum amount of personal information necessary for their purposes.
Personal information must be kept accurate and up-to-date. Websites must also implement appropriate security measures to protect personal information from unauthorized access, loss, or damage.
Websites must have a clear and concise privacy policy that explains how personal information is collected, used, and protected.
Personal information can only be transferred outside of South Africa if certain conditions are met, such as obtaining the consent of the data subject.
The POPI Act is enforced by the Information Regulator, which has the power to investigate complaints and impose fines for non-compliance.
Websites must also implement appropriate security measures to protect personal information from unauthorized access, loss, or damage.
With access controls in place / firewall with Cloud flare and updated websites meet this requirement in terms of the POPI act.